Secure Docker Image Pulls from Cloudsmith to Kubernetes using OIDC
Explore how to use OpenID Connect (OIDC) to enable Kubernetes to pull Docker images from Cloudsmith without relying on long-lived credentials. This approach significantly enhances security and simplifies credential management.

In the world of containerised applications, securely pulling Docker images from private registries is a common challenge. Today, we'll explore how to use OpenID Connect (OIDC) to enable Kubernetes to pull Docker images from Cloudsmith without relying on long-lived credentials. This approach significantly enhances security and simplifies credential management.
The Challenge: Secure Image Pulling
Kubernetes clusters often need to pull Docker images from private registries like Cloudsmith. Traditionally, this required storing long-lived credentials in the cluster, which poses several security risks:
- Credentials could be compromised if the cluster is breached.
- Regular rotation of credentials becomes a manual, error-prone process.
- It's difficult to apply the principle of least privilege effectively.
Understanding Image Pull Secrets
Before we dive into the solution, let's quickly review what an Image Pull Secret is in Kubernetes.
An Image Pull Secret is a way to pass credentials to the kubelet for authenticating with a private container registry. Typically, these secrets contain:
- The registry URL
- A username
- A password or access token
While Image Pull Secrets solve the immediate problem of authentication, using them with long-lived credentials still leaves us exposed to the security risks mentioned earlier.
The OIDC Solution
OpenID Connect (OIDC) allows us to use short-lived tokens instead of long-lived credentials. Here's how it works in the context of Kubernetes and Cloudsmith:
- Kubernetes has its own identity in the form of a service account.
- This service account has an associated JWT (JSON Web Token).
- We can exchange this JWT for a short-lived Cloudsmith token.
- We use this short-lived token to create or update an Image Pull Secret.
This process can be visualised as follows:
Automating the Process with a CronJob
To make this process automatic and seamless, we use a Kubernetes CronJob. This job runs at regular intervals and performs the following tasks:
- Retrieves the Kubernetes service account token.
- Exchanges this token for a Cloudsmith token via OIDC.
- Creates or updates an Image Pull Secret with the new Cloudsmith token.
Here's an example of what this CronJob might look like:
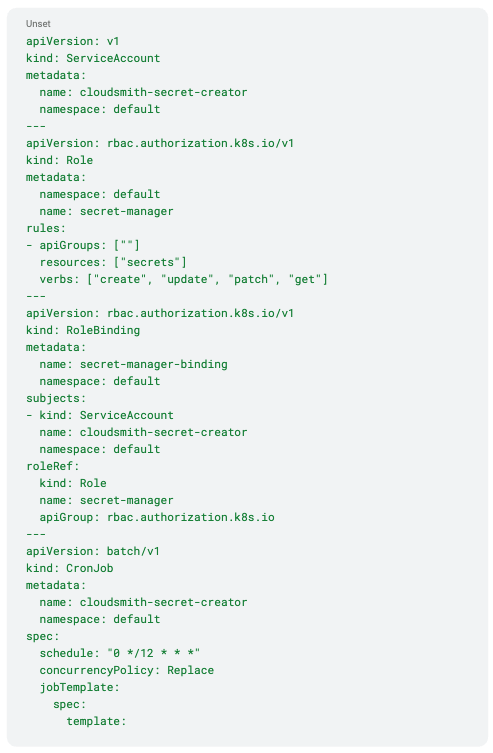
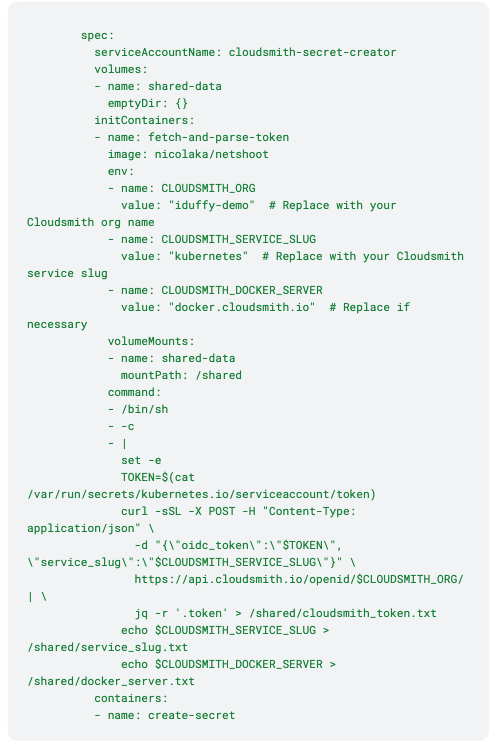
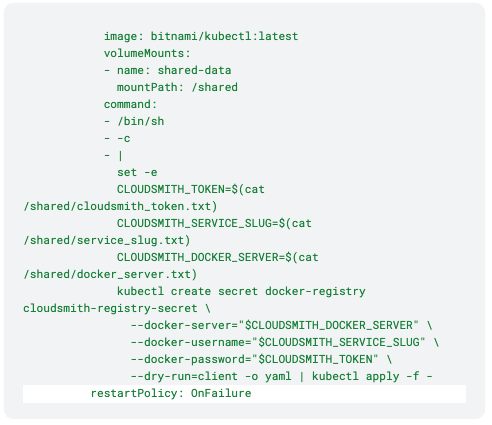
This CronJob:
1. Runs every 12 hours
2. Gets the Kubernetes service account token.
3. Exchanges it for a Cloudsmith token.
4. Creates or updates an Image Pull Secret named cloudsmith-pull-secret.
Benefits of this Approach
Implementing this OIDC-based solution offers several significant benefits:
- Enhanced Security: No long-lived credentials are stored in the cluster, reducing the risk of credential compromise.
- Automatic Rotation: The CronJob ensures the token is regularly refreshed, maintaining a good security posture without manual intervention.
- Simplified Management: There's no need to manually update credentials, reducing operational overhead.
- Principle of Least Privilege: The token has only the permissions it needs, for a limited time, aligning with security best practices.
Using the Image Pull Secret
Once the Image Pull Secret is created or updated by the CronJob, you can use it in your pod specifications like this:
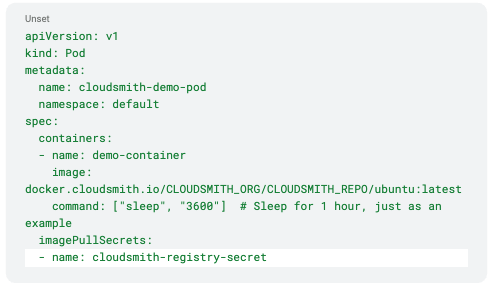
This pod will use the cloudsmith-pull-secret to authenticate with Cloudsmith and pull the specified image.
Conclusion
That wraps up our look at using OIDC to pull Docker images from Cloudsmith into Kubernetes. This approach eliminates the need for long-lived credentials. It reduces the risk of leaked credentials, removes the need for manual credential rotation, and aligns with current security best practices.
Liked this article? Don\'t be selfish (:-), share with others: Tweet
